Beyond the Transaction: Holistic Network Analysis for Advanced Fraud & AML


Introduction
Sophisticated financial criminals don’t think in single transactions; they think in networks. They build complex, evolving webs to hide their tracks, using techniques like structuring, layering, and integration that are invisible to traditional, siloed monitoring systems. To fight modern financial crime, you need to see the entire, dynamic picture. Holistic network analysis over time provides this crucial visibility, moving beyond individual alerts to reveal the underlying narrative of criminal activity.
The Blind Spot of Traditional Monitoring
Traditional AML and fraud detection systems are built to flag individual events: a large transaction, a payment to a sanctioned entity, or a transfer exceeding a specific threshold. While necessary, this approach creates a major blind spot. Criminals are experts at staying just below these thresholds. They use:
- Structuring: Breaking down large sums into many smaller transactions to fly under the radar.
- Layering: Creating long, convoluted chains of payments through multiple accounts to obscure the original source of funds.
When you only look at each transaction in isolation, you miss the coordinated pattern. You see the individual trees, but you miss the forest - and the criminal conspiracy hiding within it.
Seeing the Full Story with Temporal Graph Analytics
Pometry’s temporal graph engine allows you to move beyond single data points and build a complete, dynamic view of your entire interaction network. By consolidating terabytes of transactional data into a unified model, you can see precisely how relationships and behaviours evolve.
Our platform empowers your team to:
- Analyse at Scale: Interrogate massive, evolving networks at speeds up to 200x faster than conventional graph systems, turning hours of query time into seconds.
- Uncover Hidden Schemes: Apply a library of over 50 pre-built graph algorithms to automatically detect suspicious patterns like circular payments, unusual “hub-and-spoke” activity, and other indicators of structuring.
- Visualise the Narrative: Go beyond static charts to see how a criminal network assembles, operates, and attempts to cash out over time, providing undeniable context for investigators.
Conclusion
Stop chasing individual alerts and start dismantling criminal networks. With Pometry’s holistic network analysis, you can gain the temporal context needed to see beyond single transactions, identify sophisticated fraud and AML schemes, and give your investigators the decisive advantage they need. You can build and deploy a powerful Proof of Concept for this capability in as little as two weeks.

You might also like
Discover insights and tools for data analysis.

The hidden failures of transformation
Why delivery optimisation is making transformation worse
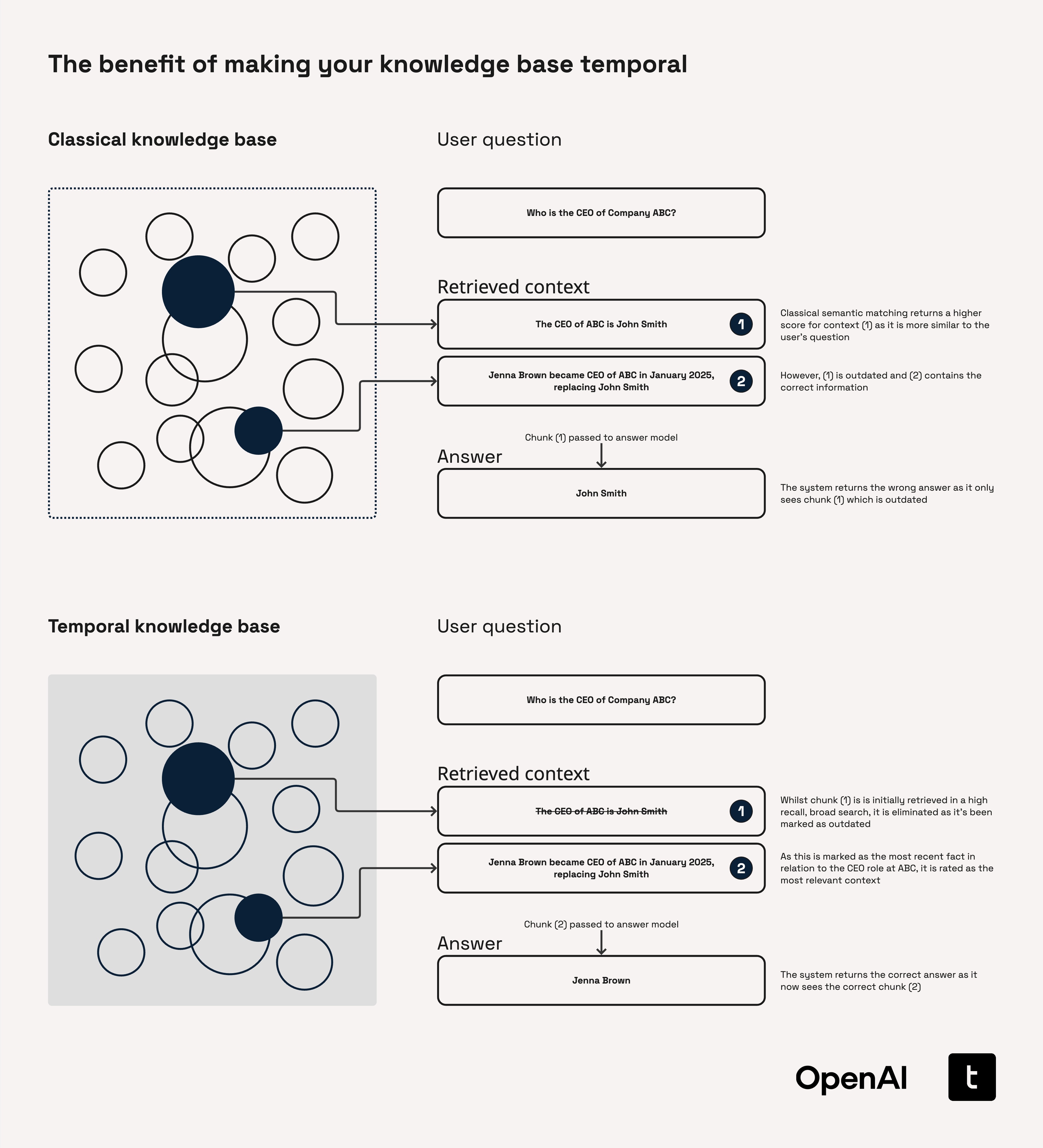
The Missing Link for AI Agents: Why a Native Temporal Graph is Non-Negotiable
Unlock Your
Data's Potential
Discover how our tool transforms your data analysis with a personalized demo or consultation.