The Grammar of Crime: Detecting Fraud with Advanced Behavioural Sequencing


Introduction
Modern financial criminals are choreographers of complex schemes. They don’t rely on a single, obvious action but on a carefully orchestrated sequence of events designed to appear legitimate in isolation. From smurfing and structuring to synthetic identity fraud, the true criminal intent is hidden in the pattern, not the individual steps. To defeat these adversaries, you must learn to read the grammar of their crimes by analysing the sequence of their actions over time.
Imagine the following scenario: John Citizen likes goes Starbucks every Wednesday, spends fives minutes in the queue, and orders a Caramel Frappuccino. If he has been doing this for the last six months, it's not hard to infer that next Wednesday, and the Wednesday after, he will be at Starbucks for five minutes to order a Caramel Frappuccino.
However, if he instead goes there and spends an hour; that's a deviation from the norm. Tracked in real-time, this allows us to trigger a timely alert and ask critical questions, such as: Who was he with? What connections do they share? Did they leave together?
It’s not just about the single ocurrence, but the routine, and the break in the pattern that provides the most valuable insight.
Why Traditional Rules Miss the Plot
Traditional rules-based monitoring systems are like a security guard who only sees people entering a building one by one. They can’t see that ten people, all arriving five, ten or sixty minutes apart, are actually a coordinated team. These systems are good at flagging singular, obvious violations but are blind to multi-step fraud typologies where each individual action is designed to be innocuous. They see the nouns and verbs of a transaction but completely miss the syntax that reveals the criminal narrative.
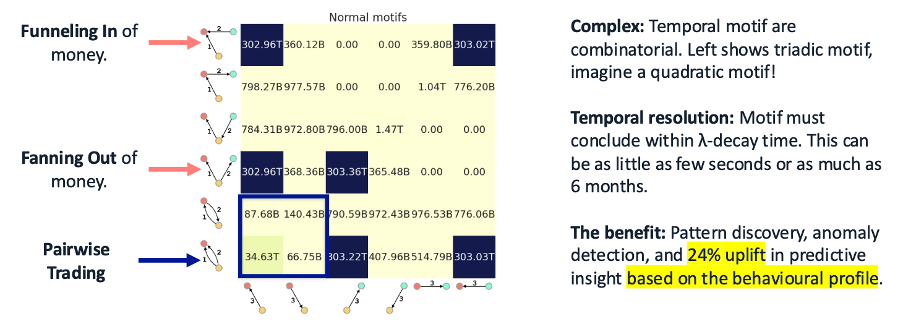
Decoding Criminal Choreography with Temporal Graphs
Pometry’s temporal graph engine is uniquely suited to detect these sophisticated behavioural sequences. By modelling every transaction and action as an event in a time-ordered graph, we provide the foundation to see the entire choreography as it unfolds.
- Define and Detect Complex Typologies that Scale: Your fraud analysts and data scientists can model and search for complex behavioural sequences directly in Python on terabytes of data and billions of relationships directly on a laptop. They can combine the power of temporal graph analytics with their existing ML models to define nuanced patterns, all while our engine executes these queries at native Rust-level speeds.
- Identify Known and Unknown Threats: Go beyond simple rules to detect the subtle grammar of known fraud typologies like bust-out schemes, trade-based money laundering, or circular payment networks. The flexibility of the engine also allows you to hunt for new and emerging attack vectors in an unsupervised, autonomous way.
- Rapidly Deploy New Defences: The agility of our platform means you can go from identifying a new fraud pattern to deploying a production-ready detection model in as little as one week, dramatically shortening your response time to evolving threats.
Conclusion
Stop reacting to the individual notes and start recognising the symphony of fraud. With Pometry’s advanced behavioural sequencing capabilities, you can move beyond static rules to detect the sophisticated, multi-step typologies used by modern criminals, giving your organisation a decisive, proactive defence against financial crime.

You might also like
Discover insights and tools for data analysis.

The hidden failures of transformation
Why delivery optimisation is making transformation worse
The Missing Link for AI Agents: Why a Native Temporal Graph is Non-Negotiable
Unlock Your
Data's Potential
Discover how our tool transforms your data analysis with a personalized demo or consultation.